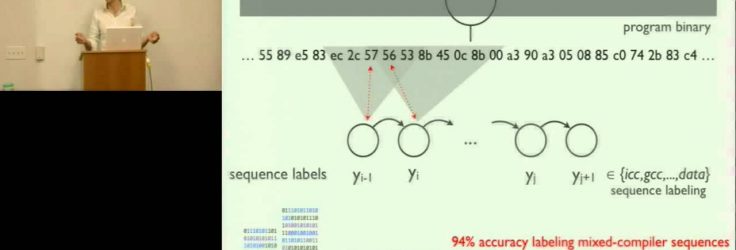
Where did this binary come from? How was it compiled? What language did the programmer choose? Who wrote this code? These questions rarely occur to most computer users, but for analysts working in forensics, reverse engineering, and software theft, they are of paramount importance. The provenance of a program binary — the specific process through which an idea is transformed into executable code — can provide valuable insight, yet it is in the very domains where such information would be most useful that it is least likely to be available.